
- Product

- Pricing
- Affiliate Program
- Use Cases
- Resource


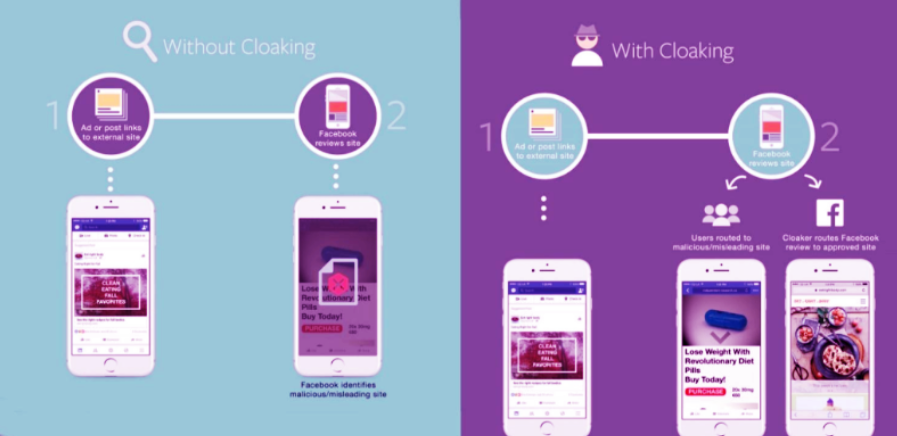
Traffic arbitrage is often associated with promoting offers that violate advertising platform policies. These may include nutra, gambling, dating, crypto, adult content, pseudomedicine, and others. To bypass moderation and avoid account bans, a technique called cloaking is used — which involves showing different content to different types of visitors.
The main goal of cloaking is to hide prohibited content from moderators and automated systems on ad platforms like Facebook, Google, TikTok, and others. Without cloaking, these types of offers won't pass moderation and may result in advertiser account bans. With cloaking, the moderator sees a compliant page (white page), while the target user is redirected to a sales landing page (black page).
Cloaking (from the English “cloaking” — masking) is a traffic segmentation technology. In arbitrage, this means that the same URL leads to different pages depending on visitor characteristics. Key deciding factors may include:
IP address and geolocation
User Agent
Device type (mobile or desktop)
Presence of VPN/proxy
Referrer
JavaScript activity and other parameters
Depending on these factors, the user is either sent to a white page or a black page.
Cloaking operates as follows: The arbitrageur prepares two versions of the landing page — a white page, which is fake but safe and compliant with ad platform rules, and a black page, which is the real sales page and may contain restricted or "gray" content. Both pages are hosted on a server or connected through a cloaking service.
Next, traffic filtering rules are set. The cloaking system collects data from each visitor: IP, geolocation, User Agent, device type, proxy/VPN use, on-page behavior, and more. These inputs are checked against pre-set rules.
The system then decides which page to show. If the traffic is identified as non-target (e.g., a Facebook, Google, or TikTok bot or user with a suspicious IP from a data center), it serves the white page, which complies with network rules — such as a clinic, gym, or informational blog. This content easily passes moderation.
If the system detects a target user — coming from the desired GEO, using a mobile device, not using anonymizers, and showing no suspicious behavior — they are redirected to the real black page, which contains the main offer: a product, service, or lead form.
Cloaking works in real time, ensuring content masking even during repeat inspections.
Cloaking is used in two main cases in traffic arbitrage:
To bypass moderation on advertising networks with strict content policies and automated filtering systems. Without content swapping, such campaigns are often rejected, and accounts get banned.
To protect campaign setups from competitors. Without cloaking, spy tools quickly detect live ads, follow the links, record the offer, and soon others copy your funnel — reducing its performance.
Cloaking typically involves several components. The core is a TDS (Traffic Distribution System) that analyzes user parameters and directs them to either the white or black page.
White page – a fake landing page meant for moderators and unauthorized visitors. It complies with ad rules and serves as a disguise.
Black page – the actual landing page where the offer is hosted and conversions happen.
To ensure accurate filtering, the system uses up-to-date databases of known IP addresses and User Agents used by bots and moderators. This helps precisely filter out unwanted visits.
Additionally, tools like MoreLogin (an antidetect browser) are often used to manage multiple isolated profiles with unique browser fingerprints. This reduces detection and bans, especially when working with multiple accounts and aggressive campaigns.
A classic setup: Traffic matching condition X → white page; traffic matching condition Y → black page. This is configured in a tracker or through a specialized service.
An intermediate page with buttons like “I’m 18+” or “Continue.” Moderators might proceed through it if they choose, making it less effective. Conversion rates may drop due to the extra step.
Some cloaking services update their databases automatically. If not, you can use public repositories:
GitHub (lord-alfred) — Facebook IP
GitHub (lord-alfred) — Google IP
General repository
There are also private databases shared in arbitrage communities and forums.
To set up cloaking in Keitaro, start by uploading two landing pages — one for moderation (white page), and one for target users (black page). Then create a new campaign in the Campaigns section and set up traffic flows.
Forced flow — for bots/moderators; leads to the white page.
Regular flow — for target traffic; leads to the black page.
Default flow — catches unfiltered traffic; also goes to the white page.
Then apply filters such as country, IP, proxy status, device type, etc. After setup, integrate the KClient PHP code into your landers to ensure proper cloaking upon each visit.
Upload the white page — e.g., a gym website.
Upload the black page — the offer landing.
Set filters: Ukraine GEO, mobile only, block proxies and empty referrers.
Insert the integration code into index.php.
The cloaker sends moderators to the gym page, users to the offer.
You get banned. Not just the ad account, but also your device, browser, and IP. Creating a new account becomes nearly impossible without an antidetect browser or aged accounts.
Use a cloaking service with auto-updating databases.
Restrict access by IP, GEO, and device type.
Don’t use white pages unrelated to the ad creatives.
Set up anti-spy protection to block competitor tracking.
Cloaking remains a crucial tool in traffic arbitrage, especially for gray and restricted offers. Its main function is to ensure ad moderation approval while protecting high-performing campaigns from copycats, and maintaining reach to the target audience.
Despite frequent updates to ad platform algorithms, cloaking still enables effective campaign launches on Facebook, Google Ads, TikTok, and other traffic sources.